Overview
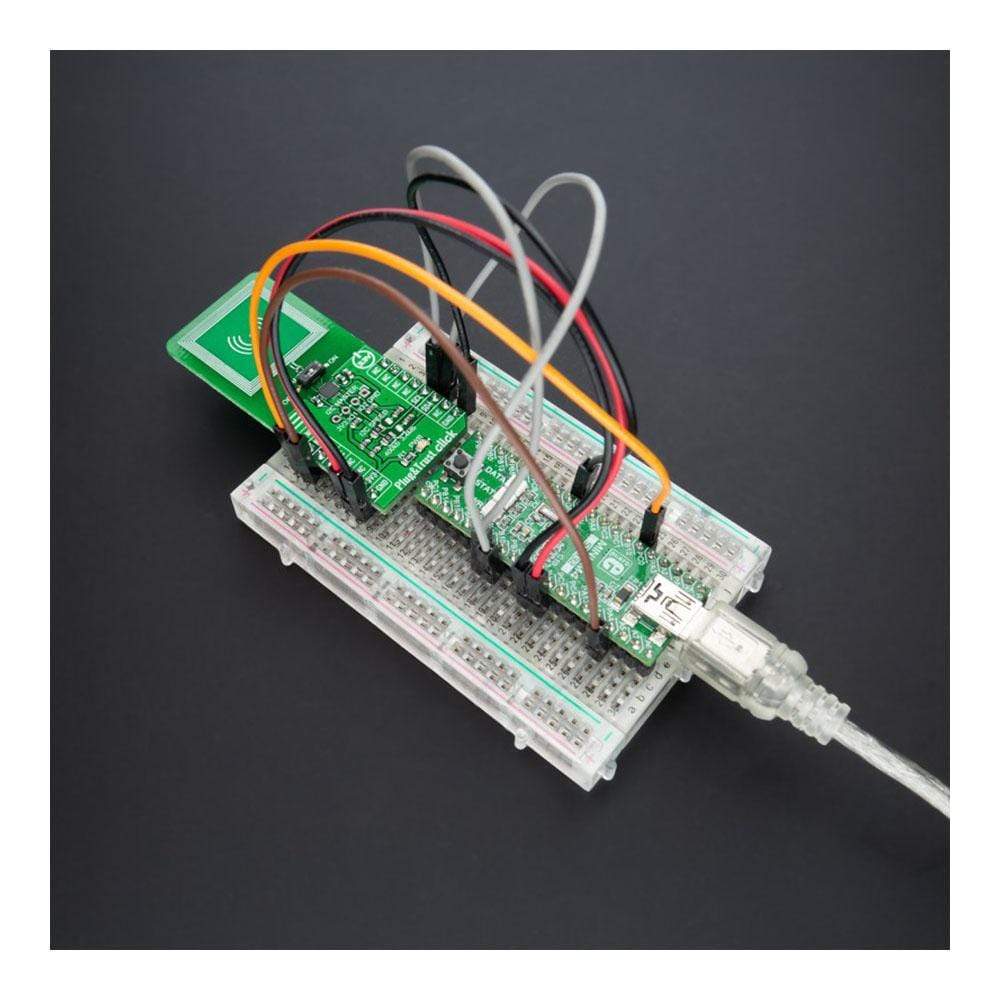
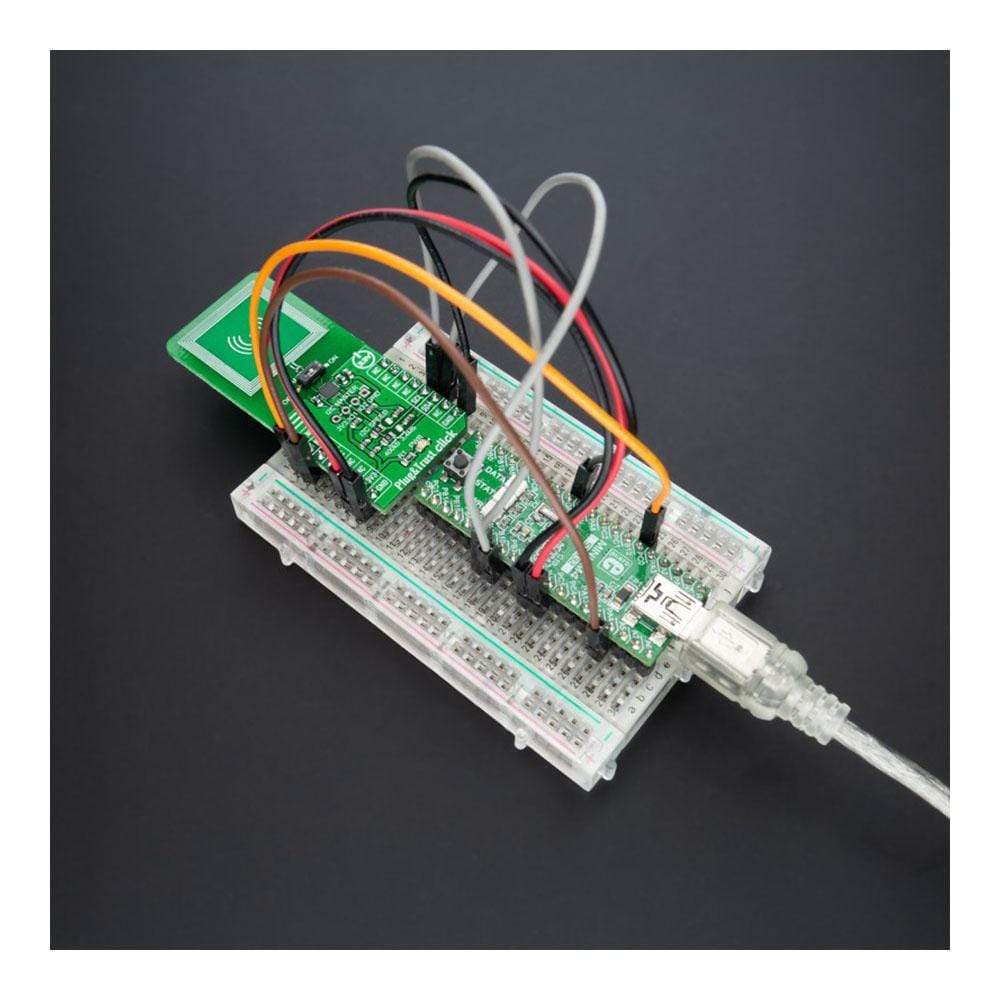
The Plug&Trust Click Board™ is a compact add-on board that contains a ready-to-use IoT secure element solution. This board features the SE050C secure element IC NXP, which provides a root of trust at the IC level, and it gives an IoT system state-of-the-art, edge-to-cloud security capability. The SE050C allows for securely storing and provisioning credentials and performing cryptographic operations for security-critical communication and control functions. It has an independent Common Criteria EAL 6+ security certification up to OS level and supports both RSA & ECC asymmetric cryptographic algorithms with high key length and future proof ECC curves, protecting the SE050C even against sophisticated non-invasive and invasive attack scenarios. This Click Board™ is suitable in IoT security use cases such as secure connection to public/private clouds, device-to-device authentication, sensor data protection, and more.
Plug&Trust Click is supported by a mikroSDK compliant library, which includes functions that simplify software development. This Click Board™ comes as a fully tested product, ready to be used on a system equipped with the mikroBUS™ socket.
Downloads
La carte Click Board™ de Plug&Trust est une carte complémentaire compacte qui contient une solution d'élément sécurisé IoT prête à l'emploi. Cette carte est dotée de l'élément sécurisé IC SE050C NXP, qui fournit une racine de confiance au niveau du circuit intégré et offre à un système IoT une capacité de sécurité de pointe, de la périphérie au cloud. La SE050C permet de stocker et de provisionner en toute sécurité les informations d'identification et d'effectuer des opérations cryptographiques pour les fonctions de communication et de contrôle critiques pour la sécurité. Elle dispose d'une certification de sécurité indépendante Common Criteria EAL 6+ jusqu'au niveau du système d'exploitation et prend en charge les algorithmes cryptographiques asymétriques RSA et ECC avec une longueur de clé élevée et des courbes ECC à l'épreuve du temps, protégeant ainsi la SE050C même contre les scénarios d'attaque sophistiqués non invasifs et invasifs. Cette carte Click Board™ convient aux cas d'utilisation de sécurité IoT tels que la connexion sécurisée aux clouds publics/privés, l'authentification d'appareil à appareil, la protection des données des capteurs, etc.
Cliquez sur Plug&Trust est pris en charge par une bibliothèque compatible mikroSDK, qui comprend des fonctions qui simplifient le développement logiciel. Cette Click Board™ est un produit entièrement testé, prêt à être utilisé sur un système équipé du socket mikroBUS™.
| General Information | |
|---|---|
Part Number (SKU) |
MIKROE-4656
|
Manufacturer |
|
| Physical and Mechanical | |
Weight |
0.02 kg
|
| Other | |
Country of Origin |
|
HS Code Customs Tariff code
|
|
EAN |
8606027382666
|
Warranty |
|
Frequently Asked Questions
Have a Question?
Be the first to ask a question about this.