

Key Features
Overview
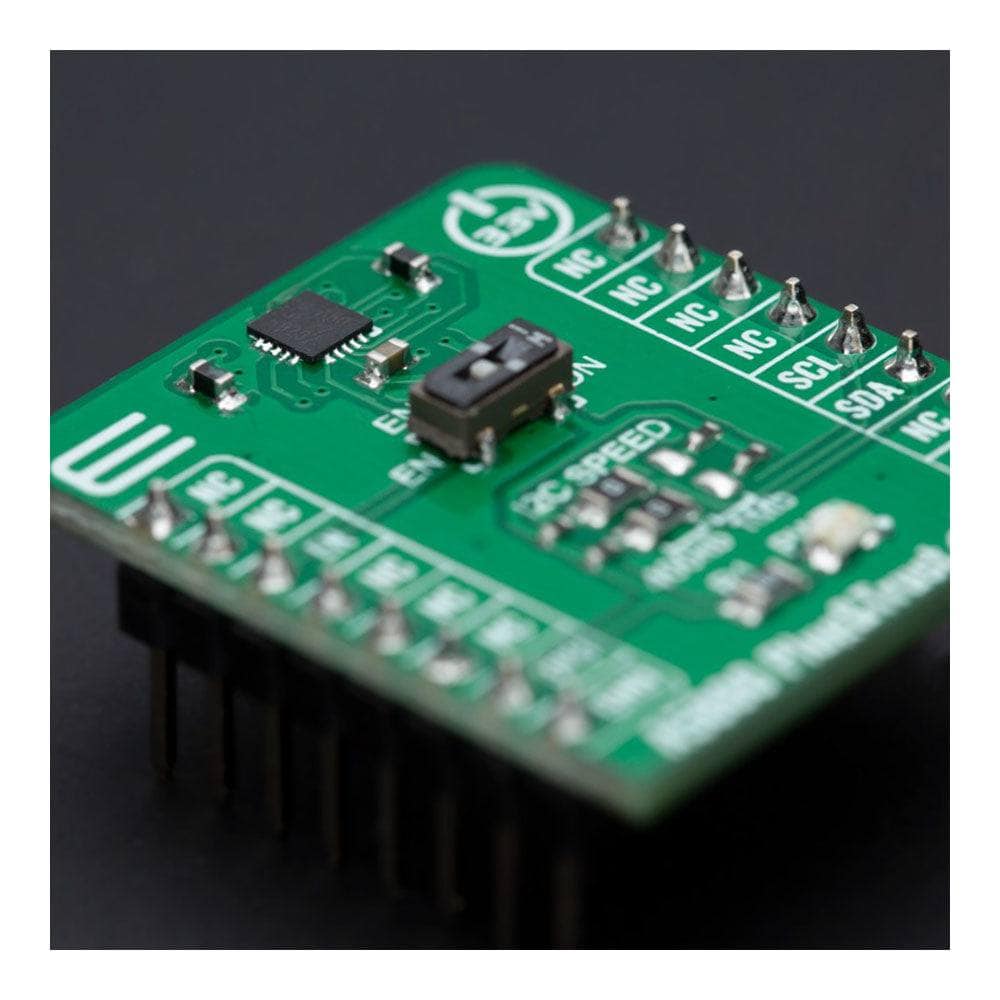
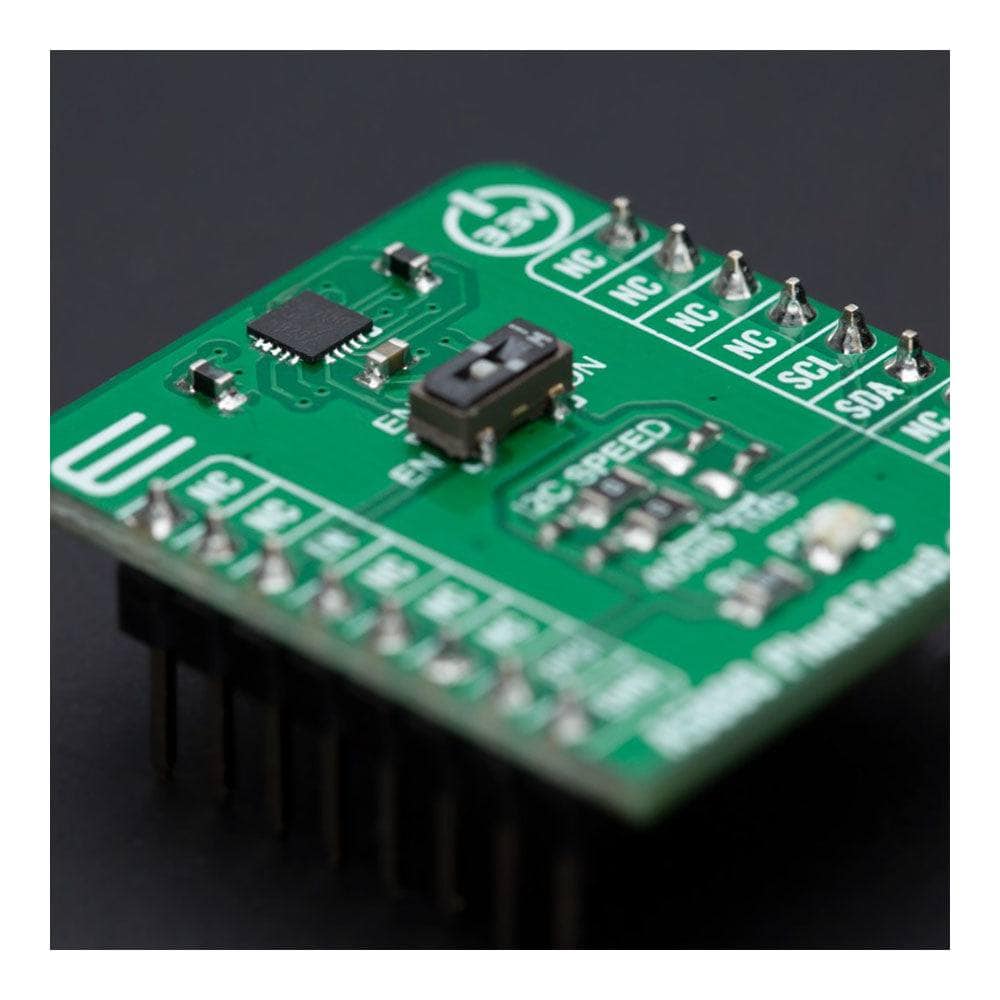
The A5000 Plug&Trust Click Board™ is a compact add-on board representing a ready-to-use secure IoT authenticator. This board features the A5000, an Edge Lock® Secure Authenticator from NXP Semiconductors. The A5000 provides a root of trust at the IC level, giving an IoT authentication system state-of-the-art security capability. It allows for securely storing and provisioning credentials and performing cryptographic operations for security-critical communication and authentication functions. It has an independent Common Criteria EAL 6+ security certification up to OS level and supports ECC asymmetric cryptographic and AES/3DES symmetric algorithms. This Click board™ is suitable in IoT security use cases such as secure connection to public/private clouds, device-to-device authentication, or counterfeit protection.
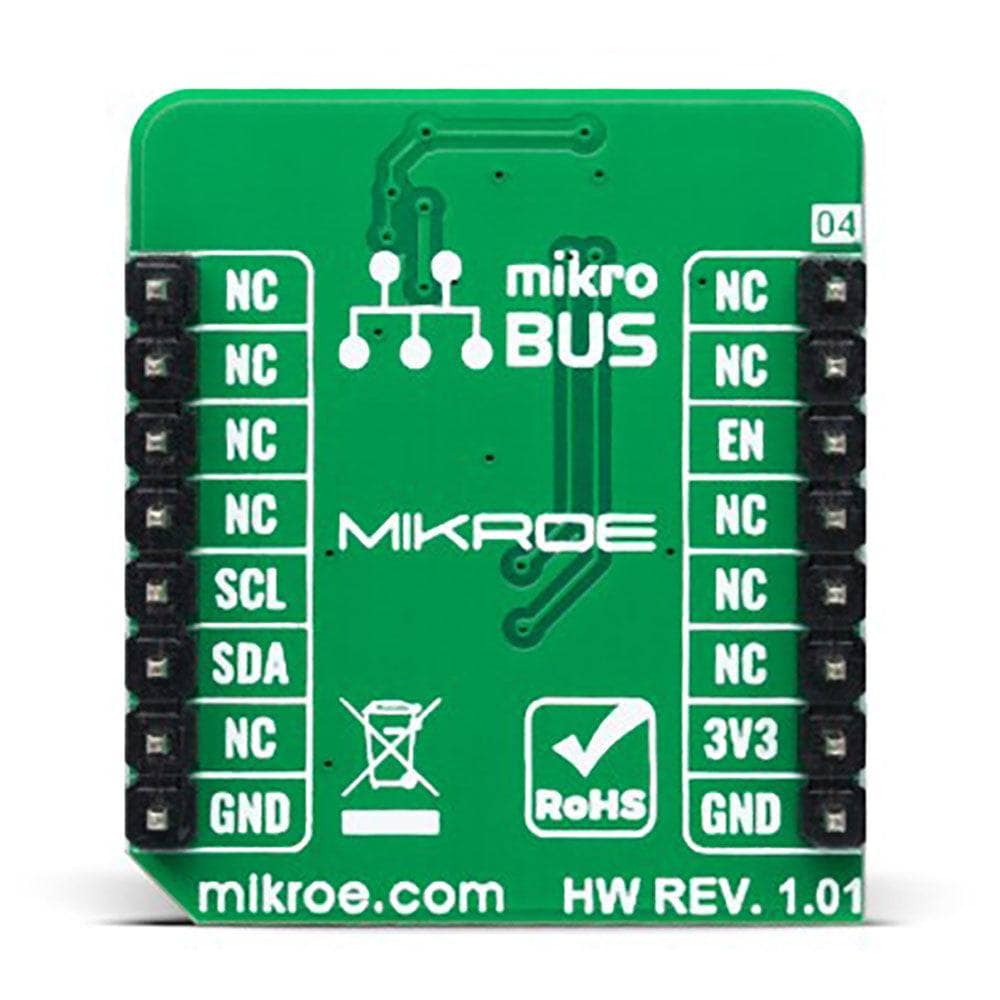
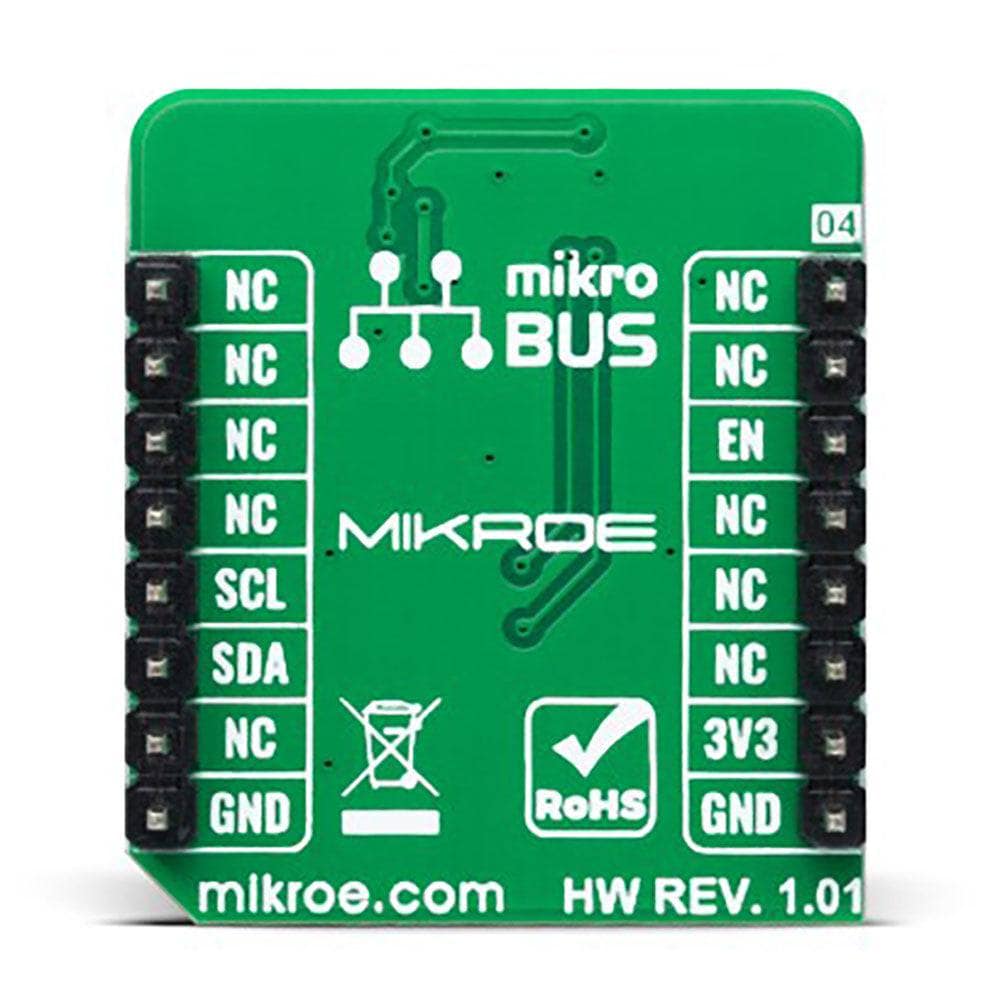
The A5000 Plug&Trust Click Board™ is supported by a mikroSDK-compliant library, which includes functions that simplify software development. This Click board™ is supplied as a thoroughly tested product, ready to be used on a system equipped with the mikroBUS™ socket.
Downloads
Das A5000 Plug&Trust Click Board™ ist eine kompakte Zusatzplatine, die einen gebrauchsfertigen, sicheren IoT-Authentifikator darstellt. Diese Platine verfügt über den A5000, einen Edge Lock® Secure Authenticator von NXP Semiconductors. Der A5000 bietet eine Vertrauensbasis auf IC-Ebene und verleiht einem IoT-Authentifizierungssystem modernste Sicherheitsfunktionen. Es ermöglicht die sichere Speicherung und Bereitstellung von Anmeldeinformationen und die Durchführung kryptografischer Vorgänge für sicherheitskritische Kommunikations- und Authentifizierungsfunktionen. Es verfügt über eine unabhängige Common Criteria EAL 6+-Sicherheitszertifizierung bis auf Betriebssystemebene und unterstützt asymmetrische ECC-Kryptografie- und symmetrische AES/3DES-Algorithmen. Dieses Click Board™ eignet sich für IoT-Sicherheitsanwendungsfälle wie sichere Verbindungen zu öffentlichen/privaten Clouds, Gerät-zu-Gerät-Authentifizierung oder Fälschungsschutz.
Das A5000 Plug&Trust Click Board™ wird von einer mikroSDK-kompatiblen Bibliothek unterstützt, die Funktionen enthält, die die Softwareentwicklung vereinfachen. Dieses Click Board™ wird als gründlich getestetes Produkt geliefert und ist einsatzbereit für ein System mit einer mikroBUS™-Buchse.
| General Information | |
|---|---|
Part Number (SKU) |
MIKROE-5391
|
Manufacturer |
|
| Physical and Mechanical | |
Weight |
0.02 kg
|
| Other | |
Country of Origin |
|
HS Code Customs Tariff code
|
|
EAN |
8606027387098
|
Warranty |
|
Frequently Asked Questions
Have a Question?
Be the first to ask a question about this.